Cybersecurity researchers today discovered the existence of a new critical vulnerability previously undetected in SIM cards, which could allow remote attackers to compromise targeted cell phones and spy on victims simply by sending an SMS message.
This vulnerability, dubbed “SimJacker”, is found in some software called S @ T Browser (a dynamic SIM card toolkit) embedded in most SIM cards that are widely used by mobile operators in at least 30 countries and can be used no matter what phones the victims use.
What bothers you? A separate private company working with governments has been actively exploiting SimJacker’s vulnerability for at least two years to conduct targeted monitoring of mobile phone users in different countries.
Also Read: Google Will Now Pay Anyone Who Reports About Apps Abusing User’s Data
S @ T Browser, short for SIMalliance Toolbox Browser, is an application that installs on various SIM cards, including eSIM, as part of the SIM Tool Kit (STK) and is designed to allow mobile operators to provide some subscription services of basis and additional wireless services for its customers.
Since S @ T Browser contains a series of STK instructions, such as sending a short message, setting up a call, starting a browser, providing local data, executing a command and sending data that can be caused simply by sending SMS to the device, the software offers a runtime environment for booting malware commands on mobile phones.
How does Simjacker vulnerability work?
Discovered by AdaptiveMobile Security researchers in a new study published today, the vulnerability could be exploited by using a GSM modem for $ 10 to perform various tasks listed below on the target device simply by sending an SMS message containing a certain type of spy code.
- Recovery of the destination device location and IMEI information,
- Spread false information by sending false messages on behalf of the victims,
- Perform premium rate fraud by dialing premium-rate numbers,
- Spy on the victims’ surroundings by ordering the device to call the attacker’s phone number,
- The spread of malware, forcing the victim’s phone browser to open a malicious Web page,
- Perform denial of service attacks by disconnecting the SIM card e
- Get more information, such as language, radio type, battery level, etc.
“During the attack, the user is completely unaware that he received the attack, that the information was extracted and that it was successfully deleted,” the researchers explain.
“Information on the location of thousands of devices was obtained over time without the knowledge or consent of the target mobile users. However, the Simjacker attack can and has been expanded to perform additional types of attacks.”
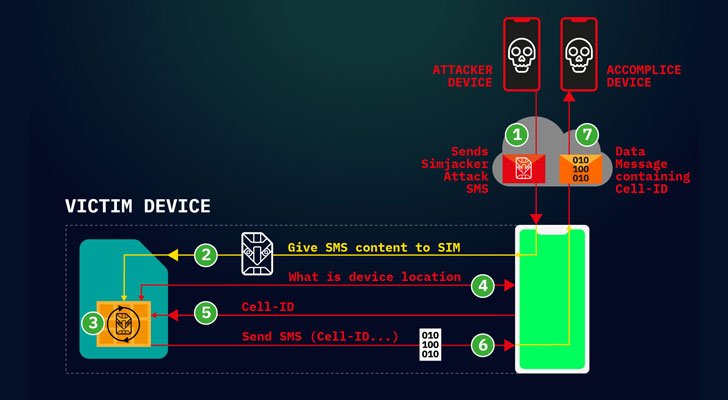
“This attack is also unique in that the Simjacker attack message can logically be classified as a load of full malware, in particular, spyware. This is because it contains a list of instructions that the SIM card must follow.”
Although the technical details, a detailed document and a proof of the concept of vulnerability are expected to be published in October of this year, the researchers said they observed real attacks on users with devices from almost all manufacturers, including Apple, ZTE, Motorola, Samsung, Google, Huawei and even IoT with SIM card -Il.
According to the researchers, all manufacturers and models of mobile phones are vulnerable to the attack of SimJacker, since this vulnerability uses an obsolete technology integrated into the SIM cards, whose specifications have not been updated since 2009, which potentially puts at risk more than one billion people.
Simjacker Vulnerability Being Exploited
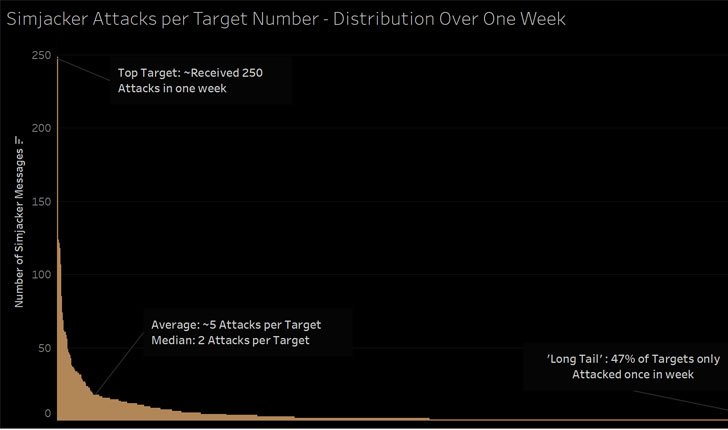
The researchers say that the Simjacker attack worked very well and has been used successfully for many years, “because it used a combination of sophisticated interfaces and dark technologies, demonstrating that mobile operators cannot rely on the security features installed standard”.
“Simjacker is a clear danger to operators and mobile subscribers. This is potentially the most sophisticated attack that has ever existed on major mobile networks,” said Ketal MacDade, CTO of Adaptive Mobile Security in a press release.
Also Read: Various WordPress Plugins Under Exploit To Direct Traffic To Malicious Websites
“This is the main warning sign that hostile actors are investing heavily in increasingly sophisticated and creative ways to undermine network security.” This threatens the security and trust of customers, mobile operators and affects the national security of entire countries “.
Furthermore, now that this vulnerability has been publicly disclosed, researchers expect hackers and other attackers to “develop these attacks in other areas”.
The researchers have revealed in a responsible way the details of this vulnerability of the GSM Association, a commercial organization that represents the community of mobile operators, as well as the SIM alliance, which represents the main producers of SIM / UICC cards.
SIMalliance acknowledged the problem and provided recommendations to manufacturers of security SIM cards for S @ T push messages.
Mobile operators can also immediately eliminate this threat by setting up the process of analyzing and blocking suspicious messages containing S @ T browser commands.
As a potential victim, it seems that the user of the mobile device cannot do anything if he uses a SIM card with the S @ T Browser technology installed on it, except for a request to replace his SIM card, on which mechanisms are installed patented security features.




An impressive share! I have just forwarded this onto a
friend who had been doing a little homework on this.
And he actually ordered me dinner because I discovered it for him…
lol. So let me reword this…. Thanks for the meal!!
But yeah, thanx for spending the time to talk about this issue here on your web page.