Hello, In this article you will learn how to hack wifi WPA / WAP2 wps enabled or locked or unlocked or network. This is one of the best methods to hack wifi without using the word list or the Reaver or any other method. This method is called EVIL TWIN ATTACK. Hack Wifi Using Evil Twin Attack creates a new false access point and attracts the victim to enter their password. Unlike other methods, the potential of this method to hack the wifi password is 95%, only a few routers are protected against the evil twin attacks.
No Reaver no WordList nonnormal turns – The best way to hack wifi on Linux
Also Read: How To Hack Wifi Password using Aircrack ng With Video Demonstration
Evil Twin attack creates a false access point as the network we want to hack and authenticator and stops its network connectivity. Then, the victim tries to connect to your network to find the new network with the same name as your network and connects to it, so that Windows is disconnected from its original network and connects to the fake free network and in which it appears a new web page that asks the victim to enter your wifi password and unless you enter, cannot access wifi. That’s how it works, it’s easy, simple and the best way to hack wifi used easily wordlist.
THIS IS FOR PURPOSES ONLY EDUCATION, I AM NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITY OF VISITORS IT’S ONLY FOR ETHICAL PURPOSES
Also Read: How To Hack Wifi Password Through Wifiphisher?
What is Evil Twin Attack?
An evil twin is a fake Wi-Fi access seems to be legitimate, configured to capture credentials in wireless communications. The evil twin method is the same as phishing. The Evil twin method creates a new phishing page that sends credentials over a local network.
This type of attack can be used to steal the passwords of unsuspecting users, either by controlling their connections or by phishing, which involves setting up a fraudulent website and attracting people there. -low. Often, users do not know that they were hacked well after the incident.
How does Evil Twin Attack work?
False access points are configured by configuring a wireless card to act as an access point (known as hostap). They are difficult to follow because they can be disabled instantly. the fake access point can receive the same SSID and BSSID a nearby Wi-Fi network. The Evil Twin can be configured to transmit Internet traffic to the legitimate access point connection while the victim is being monitored, or you can simply say that the system is temporarily unavailable after obtaining a username and password.
Also Read: How To Hack WiFi WPA2 Password Using Fluxion Tool In Kali Linux
Why the evil attack?
The bad double attack, also known as double point method access is one of the most famous and powerful attacks used by most hackers to hack wireless networks. In fact, this process is very difficult when you’re done directly, so here in this tutorial, I’m using a tool called linset, which has everything needed for the evil twin attack tools. Evil Twin attack requires the dhcp3 server and other tools during the installation causes many errors. Then using Evil Twin Attack using line to hack the wifi is the best option.
Evil Twin Attack Process
1) Scanning networks.
2) Select the network.
3) Capture the handshake (can be used without handshake)
4) We chose one of several web interfaces adapted for me (thanks to the collaboration of the users)
5) Fit a FakeAP that mimics the original
6) Create a DHCP server in FakeAP
7) Create a DNS server to redirect all requests to the host
8) the web server is started with the selected interface
9) Launch of the mechanism for verifying the validity of passwords to be introduced
10) Desauthentifica to all network users, hoping to connect to FakeAP and enter the password.
11) The attack will stop after checking the correct password
Requirements To Hack Wifi Password Without using Wordlist
1) Laptop
2) WifiSlax (Operating System)
3) Linset (Mostly Inbuilt)
4) Pendrive or Flash Drive (2gb or higher)
5) Universal USB Installer
Also Read: How to kill somebody’s Wifi in a Network
Software Requirements for Linset
Aircrack-ng
Aireplay-ng
Airmon-ng
Airodump-ng
Awk
Curl
Dhcpd
Hostapd
Iwconfig
Lighttpd
Macchanger
Mdk3
Php5-cgi
Pyrit
Python
Unzip
Xterm
As it’s a BASH script, there’s quite a list of external apps required to perform evil twin attack successfully, so we use Linset.
What is WifiSlax and Why WifiSlax
Wifislax is one of the best Spanish Linux Operating systems. It is one of the most famous operating systems for wifi hacking, to be precise this Linux based operating system is for hacking wifi networks. WifiSlax has all inbuilt tools required to hack wifi, of course, linset as well. So for this tutorial, I am using WifiSlax.
Download WifiSlax 64-bit Download WifiSlax 32-bit Alternate Download Link
How To Hack Wifi Using Evil Twin Attack Using Linset
[sociallocker id=1998]
Step 1: Install WifiSlax in Flash Drive or Pendrive using universal USB installer
Step 2: Start WifiSlax
1) Click on “Change To English Menu”

2) Click on “Run with SMP Kernel”
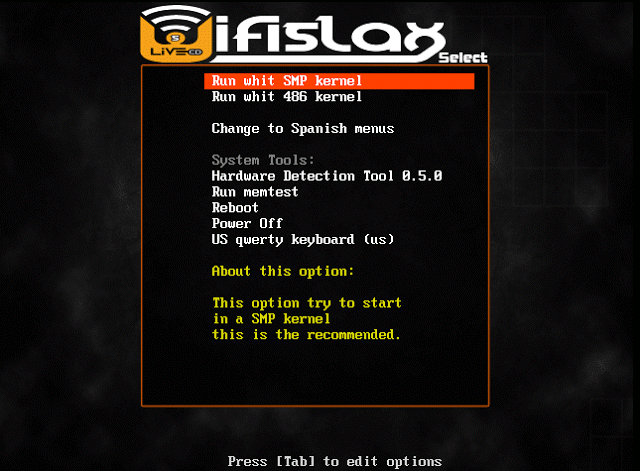
3) Click on “WifiSlax with KDE Desktop”
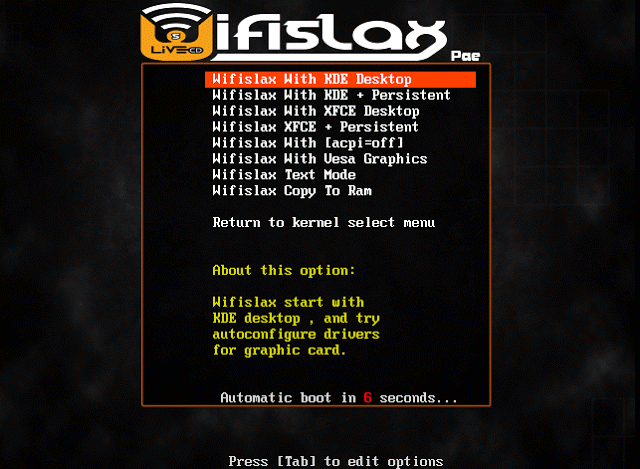
4) That’s it WifiSlax will start now
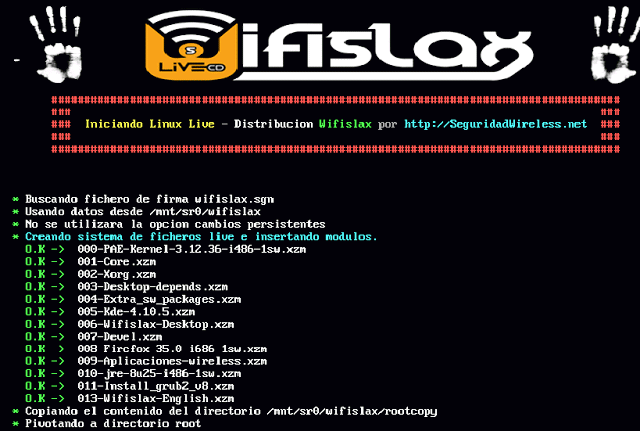
Step 3: Go to WifiSlax à WPA à Linset (Evil Twin Attack)
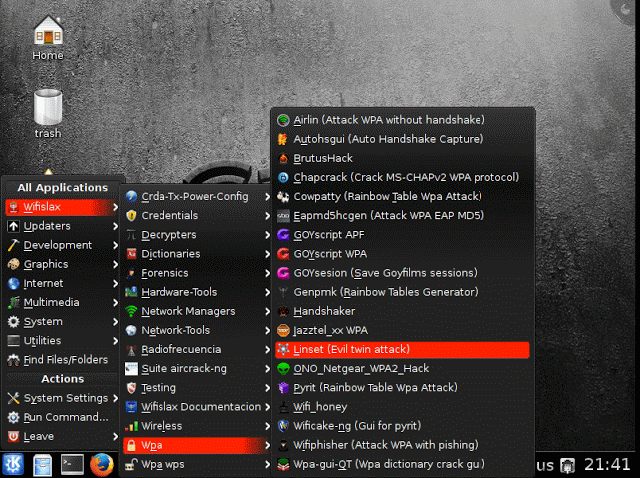
Step 4: Linset will Start required Tolls
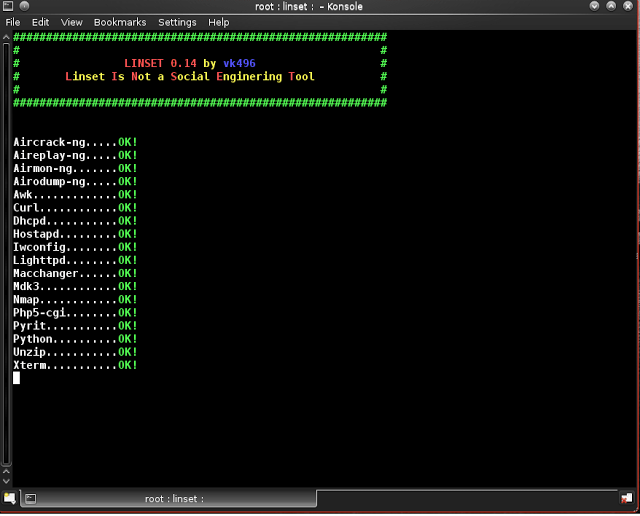
Step 5: Select Wlan0
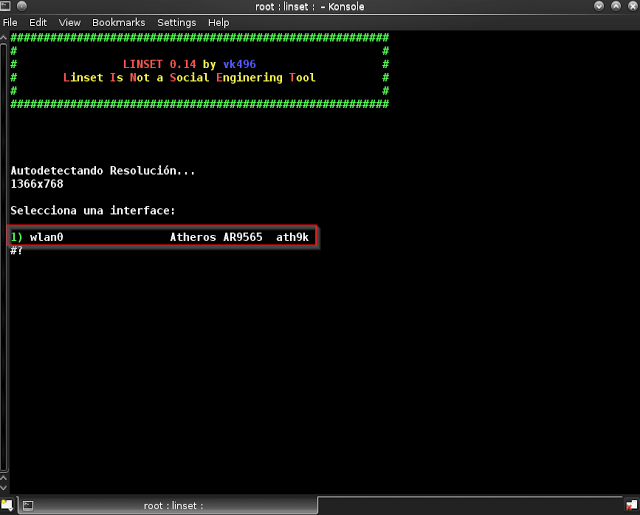
Step 6: type “1” to select Wlan0
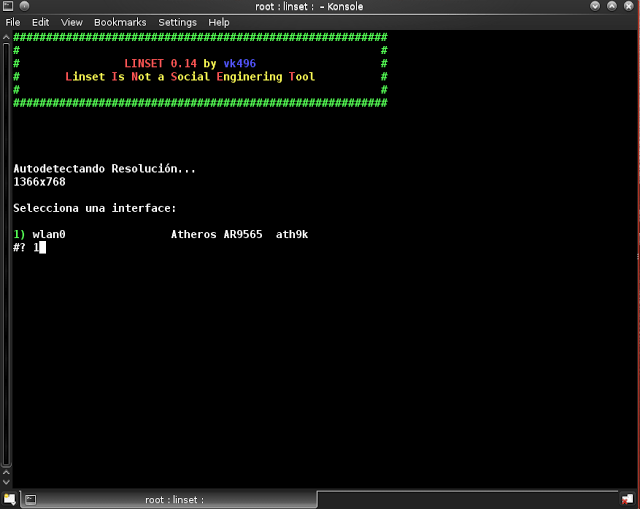
Step 7: Enter “1” to select “todos los canales” which means select all channels. We need to search all channels to get all the networks available near you. If you want to hack a particular network whose channel number you know already, select 2 and proceed.
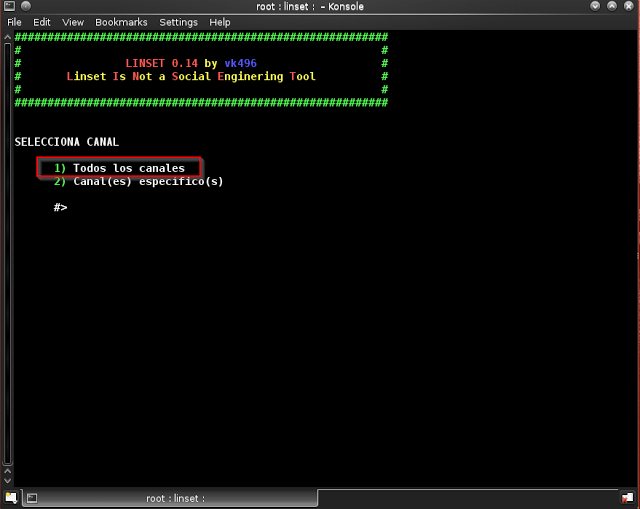
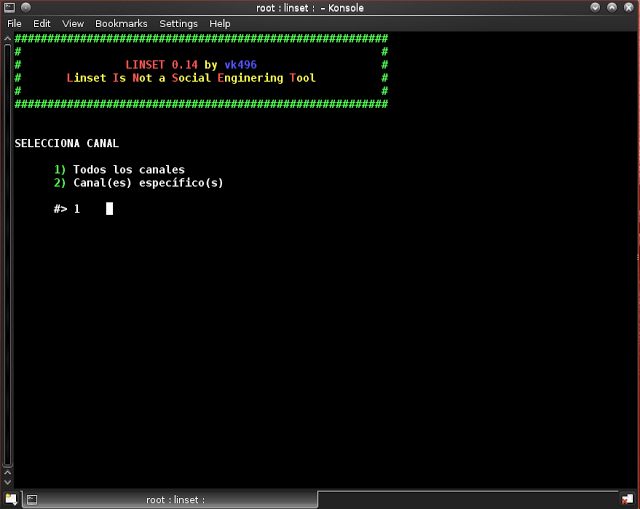
Step 8: All the Available networks will be shown now, wait for 2-3 mins to complete the search and click “CTRL +C” To stop the search
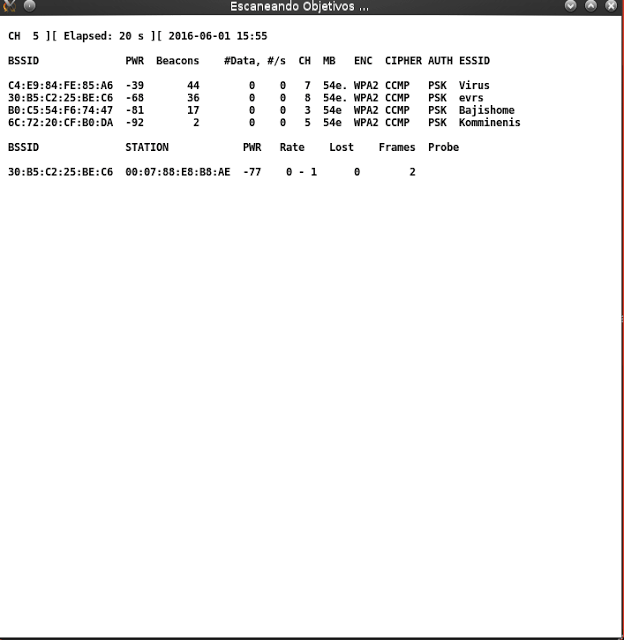
Step 9: Select the network that you want to hack from the list shown as in the below picture
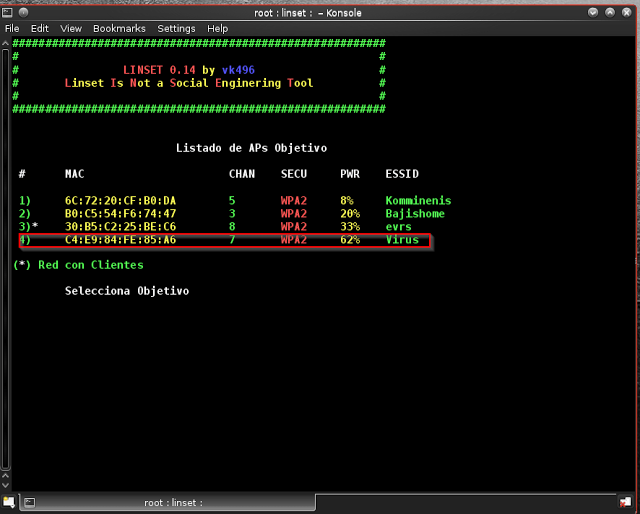
Step 10: Enter the number of the network that you want to hack, in my case, I am hacking my own network which is “Virus” and is located at number 5
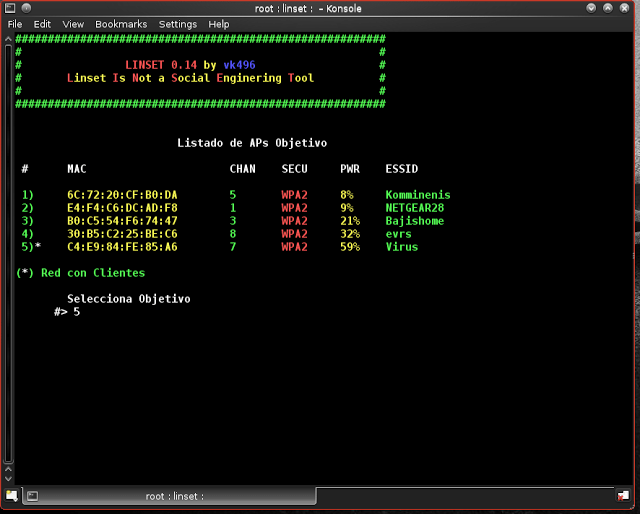
Step 11: Now we need to select hostpad, so type “1”
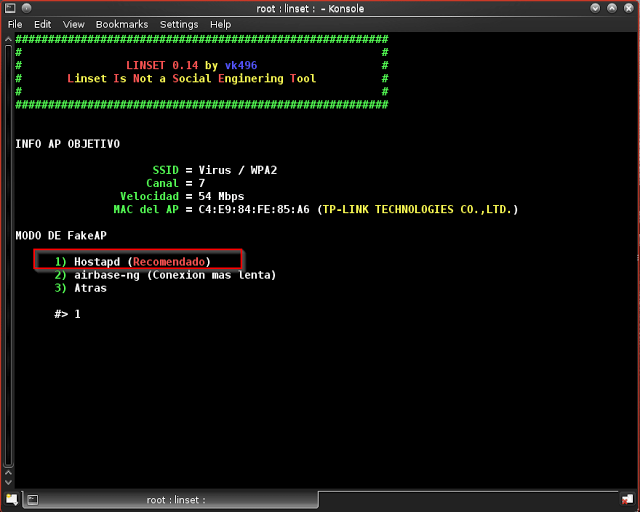
Step 12: we need to enter the path of the handshake, there is no need to enter any address, by default it takes some root/micaprura.cap, so just Hit “Enter” without typing anything
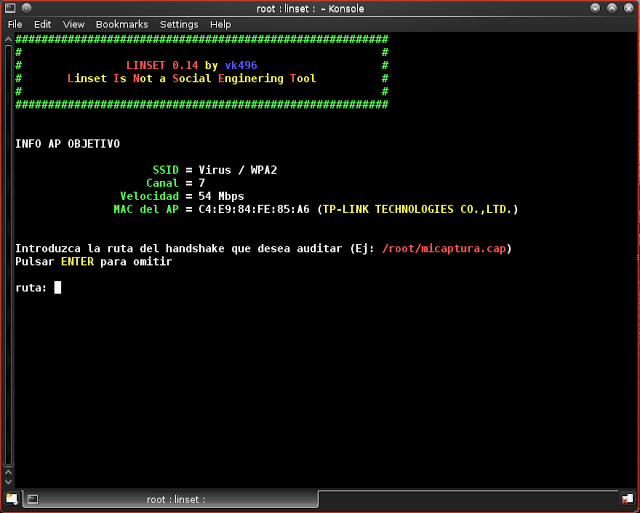
Step 13: we are going to capture handshake using aircrack-ng, so enter “1”
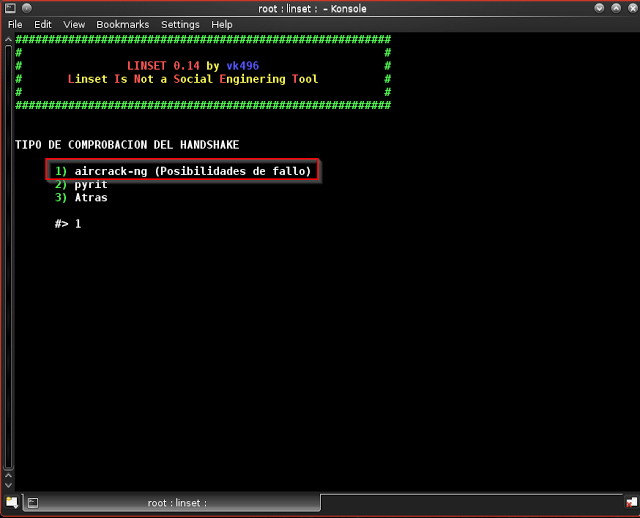
Step 14: we need to deactivate the process after the handshake is created, so we need to select “realizar desaut. masiva al ap objetivo” that is “1”
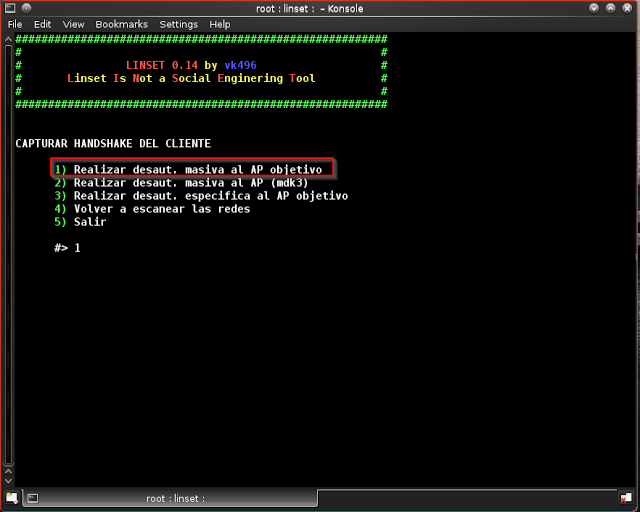
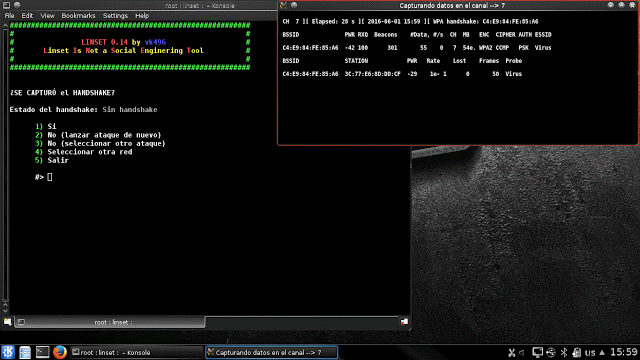
Step 15: Now Handshake capturing process will start, and 2 windows will open. we need to wait until the handshake is created. You need to capture handshake compulsorily to proceed.
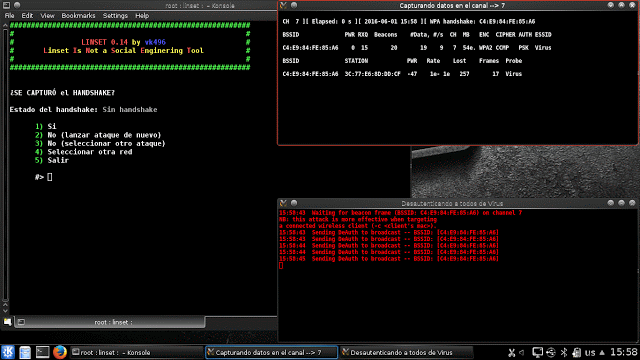
Step 16: After the Handshake is captured, close the de authentication box
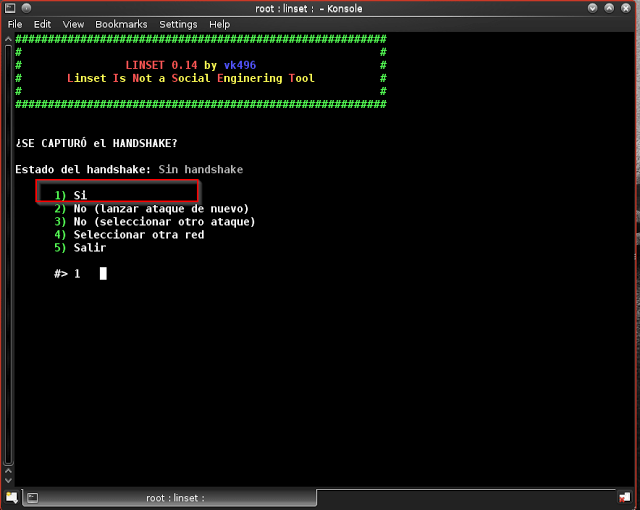
Step 17: Select “Si” which means “Yes”. So, Enter “1”
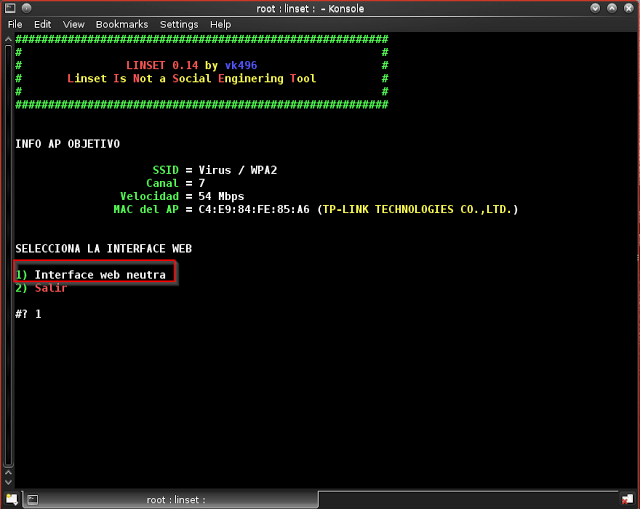
Step 18: Select “Interface Web Nutra”. So, Enter “1”
Step 19: Select your Language, I am Selecting “English” as the content in my country is displayed in English. You can choose accordingly and enter the number
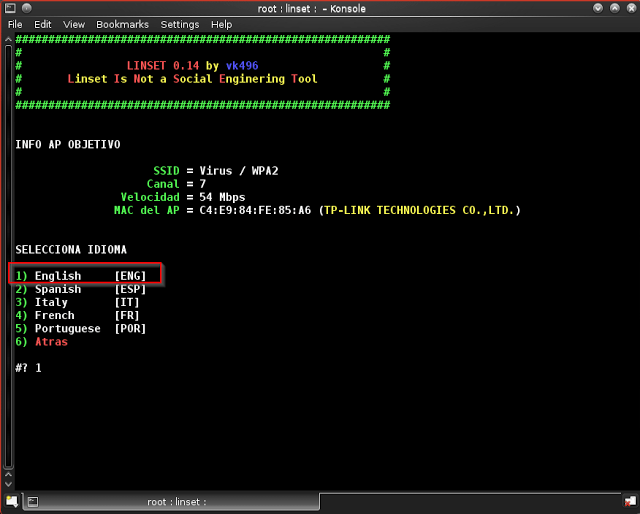
Step 20: Now the main process will start DHCP, fake DNS, AP, deauth all, and wifi info dialog boxes will open. You need to wait until the client is connected to our network.
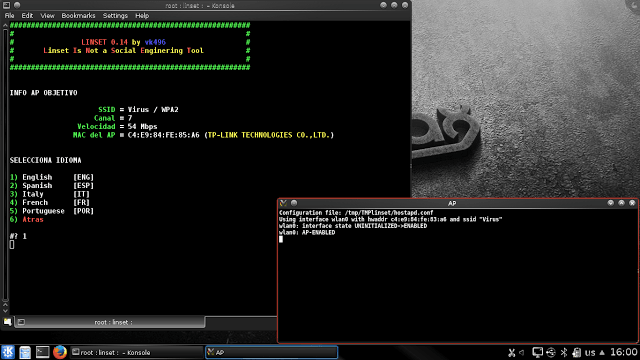
Step 21: Check out for active clients. The victim cannot access their internet connection until we stop the process. DHCP and deauth all will stop them from receiving any packets which make them shift to another network i.e. our fake access point or fake network signal
In this process, A DOS attack is launched and the victim loses their internet connection and the victim see’s it as “Limited Connection”
When you are at this step, you can even eavesdrop on the victim. you can see all the websites they surf, each and every detail is displayed in FAKE DNS
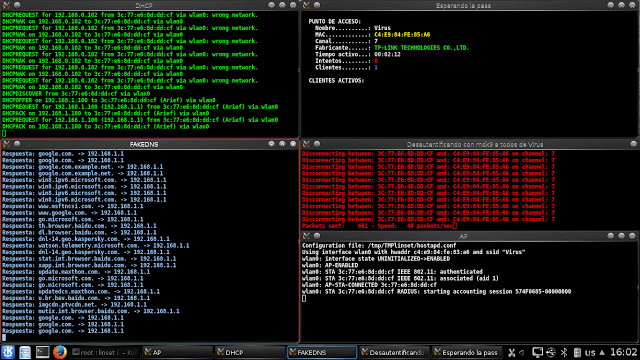
Now I will show you what happens when the process is started
Original network gets disconnected and our newly created fake network with the same name connects to victim’s network and a page pop’s up
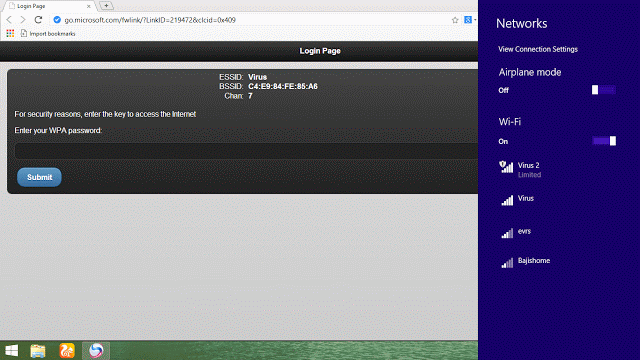
This is the page that appears, page changes from language to language, as I selected English – content is displayed in English
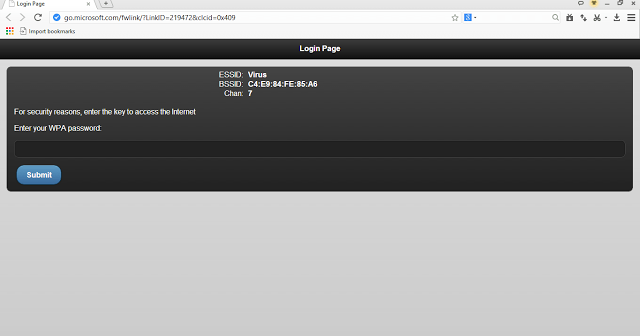
Unless the victim enters the password, they can neither access the internet nor move away from the page.
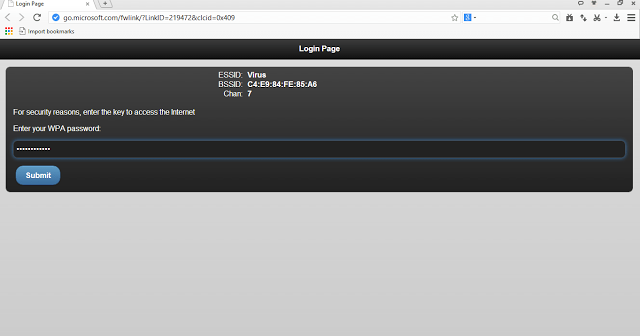
After Victim enters the password, they can get access to their old network.
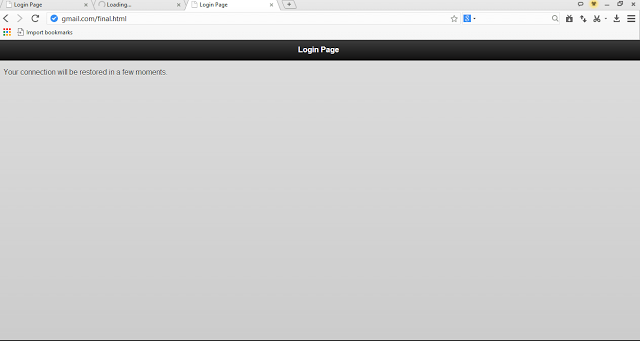
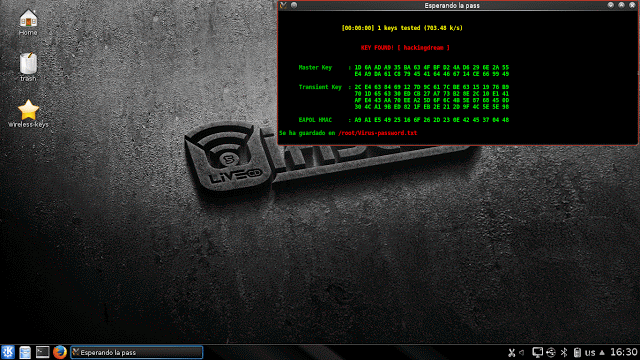
Step 22: After the victim enters the password it will be immediately shown in our window.
[/sociallocker]
So, this is how we easily decrypt any type of wifi password using dual Evil attack or false access point method. As it works without a list of words and without reaver, this is one of the best methods available to hack wifi WPA / wap2 – enabled wps and even blocked networks.
Also Read: Wifi Hacking Apps For Android (Root Required)
How to protect yourself from Evil Twin Attack?
1) Do not connect to public networks, everyone can smell your data while in a public network. The Twin Throw attack will be done as a public network, so restrict as much as possible the connection to all open or public networks mainly if the wifi name is the same as your wifi name
2) When the Internet connection stops working suddenly, it can be under DOS attack using a double evil attack, just restart the router and the attacker must restart the attack and it takes time. Maybe they will leave or continue at another time
3) Run a VPN to ensure that all browsing and data transmission is performed through an encrypted tunnel that can not be easily spied.
4) Do not always trust the name of the network, make sure it is a legitimate and reliable network or not.
========== Piracy does not need chords ==========
Just remember one thing: you do not need to ask anyone’s permission to hack anything or anyone, as long as it’s ethical, this is the main premise of the Official Hacker.
Thank you for reading my message, I hope it will be useful



when the victim enters the password in fake AP other tabs
i e AP DCHP with automatically close..
Fantastic, i was looking for this kind of content! Tks