Almost years again, we warned users approximately publicly on hand MongoDB instances – almost six hundred Terabytes (TB) – over the internet which require no authentication, probably leaving websites and servers liable to hacking.
these MongoDB instances weren’t exposed because of any flaw in its software program, but due to a misconfiguration (horrific safety exercise) that let any remote attacker get admission to MongoDB databases without the usage of any unique hacking tool.
MongoDB later resolved the problem in the next version of its software via putting unrestricted far off get admission to via default inside the configuration, heaps of web site administrators have now not updated their servers but trust me, they may now regret this!
A Hacker is now hijacking and wiping out unsecured MongoDB databases, but keeping a duplicate of those databases for asking directors a ransom of zero.2 Bitcoins (nearly US$211) to return the misplaced records. So, admins without backups are left in a bind.
In reality, the growing charge of Bitcoin even hints at a number of its problems. at the time of writing, 1 Bitcoin = $1063.93.
safety researcher and co-founder of the GDI foundation Victor Gevers (@0xDUDE) discovered the attacks and notified exposed non-password-protected MongoDB installations to proprietors through Twitter.
Gevers identified nearly 200 instances of a MongoDB set up that’s been erased and held for ransom, at the same time as this variety reached approximately 2,000 databases as of 4:00 p.m, as reported using John Matherly, the founding father of Shodan, in which many uncovered MongoDB databases can be located.
Also Read: Romanian Police Arrested 5 People For Spreading Cerber Ransomware
Those assaults have been taking place for over per week, targeting servers all around the international. it’s miles believed that in place of encrypting the information, the attacker who goes by way of the call “harak1r1,” ran a script that changed the content material of the database with the attacker’s ransom note.
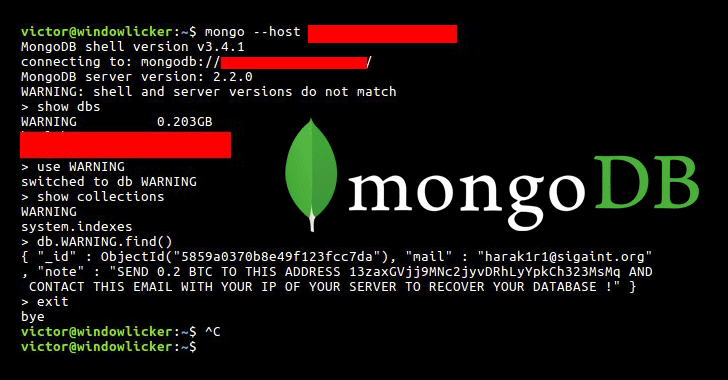
Whilst getting access to one of the open servers, Gevers determined that during the vicinity of the database content, there may be best one table, named “warning,” which reads:
“ship zero.2 BTC TO THIS cope with 13zaxGVjj9MNc2jyvDRhLyYpkCh323MsMq and get in touch with THIS email along with the IP OF YOUR SERVER TO recover YOUR DATABASE !”
It seems that around 16 groups thus far have paid the ransom to the attacker.
Matherly has been cautious of the risks of exposed MongoDB installations when you consider that 2015, allowing an attacker to remotely get right of entry to the databases over the internet without the want of any form of authentication.
Matherly said the majority of publicly exposed 30,000 MongoDB instances run on cloud servers which include Amazon, virtual Ocean, Linode, and net service and website hosting issuer OVH and achieve this without authentication, making cloud offerings buggier than data center website hosting.

Way to understand in case you’ve Been Hacked?
Take a look at the MongoDB money owed to peer if nobody added a secret (admin) person.
take a look at the GridFS to appearance if a person saved any documents there.
check the log files to a peer who accessed the MongoDB.
Way to shield yourself?
Allow authentication that offers you ‘protection in-depth’ in case your community is compromised. Edit your MongoDB configuration file — auth = true.
Use firewalls — Disable remote get entry to to the MongoDB, if feasible. Admins are advised to use firewalls to defend the MongoDB installations via blockading get right of entry to port no. 27017.
Configure Bind_ip — restriction access to the server via binding neighborhood IP addresses.
improve — administrators are strongly endorsed to upgrade their software to the latest release.
MongoDB is the most famous, open-supply No SQL database used by businesses of all sizes, from eBay and Sourceforge to The new york times and LinkedIn. directors are encouraged to follow a protection tick list furnished with the aid of the enterprise.
Nearly two years back, we warned customers approximately publicly reachable MongoDB times – almost 600 Terabytes (TB) – over the net which require no authentication, potentially leaving websites and servers at risk of hacking.
Those MongoDB times weren’t uncovered because of any flaw in its software, however because of a misconfiguration (horrific security exercise) that allows any remote attacker to get entry to MongoDB databases without the use of any special hacking tool.
MongoDB later resolved the difficulty inside the next version of its software program with the aid of setting unrestricted faraway gets entry to through default in the configuration, thousands of web page directors have no longer updated their servers yet. however consider me, they may now remorse this!
A Hacker is now hijacking and wiping out unsecured MongoDB databases, but maintaining a replica of these databases for asking directors a ransom of zero.2 Bitcoins (almost US$211) to return the misplaced statistics. So, admins without backups are left in a bind.
In truth, the growing charge of Bitcoin even guidelines at some of its troubles. at the time of writing, 1 Bitcoin = USD1063.93.
Security researcher and co-founding father of the GDI basis Victor Gevers (@0xDUDE) discovered the attacks and notified exposed non-password-covered MongoDB installations to proprietors via Twitter.
Gevers identified nearly two hundred times of a MongoDB set up that is been erased and held for ransom, at the same time as this number reached about 2,000 databases as of 4:00 p.m, as pronounced by using John Matherly, the founding father of Shodan, where many exposed MongoDB databases may be located.
Those attacks have been happening for over every week, targeting servers everywhere in the global. it is believed that as opposed to encrypting the data, the attacker who is going using the call “harak1r1,” ran a script that replaced the content material of the database with the attacker’s ransom word.
At the same time as gaining access to one of the open servers, Gevers located that in the vicinity of the database content, there is handiest one desk, named “caution,” which reads:
“ship zero.2 BTC TO THIS deal with 13zaxGVjj9MNc2jyvDRhLyYpkCh323MsMq and call THIS e-mail with the IP OF YOUR SERVER TO recover YOUR DATABASE !”
How to Stay Safe from this on the next page…!




Great blog here! Also your site loads up fast! What web host are you using?
Can I get your affiliate link to your host? I wish my site loaded up as fast as yours lol
Thanks for writing this! I visit your blog fairly often and I always feel more intelligent afterwards.
I shared this post on Facebook and my friends thought it was great too.
Anyhow, I just wanted to tell you that I appreciate
what you’re doing here. Sincerely, Your #1 fan! lol :
)
Superb blog you have here but I was wanting to know if you knew of any
message boards that cover the same topics talked about in this article?
I’d really love to be a part of community where I can get suggestions from other knowledgeable people that share the same interest.
If you have any suggestions, please let me know.
Thank you!