Project Protego CIA’s Secret Missile Control System Unveiled By Wikileaks. Each week since March, WikiLeaks has lost the secrets of the United States Central Intelligence Agency (CIA), which focuses mainly on the monitoring techniques and hacking tools used by its agents.
However, this time, the signaling organization has released something different from the previous losses of the 7th vault, because it is not piracy and espionage; instead, it is a missile control system.
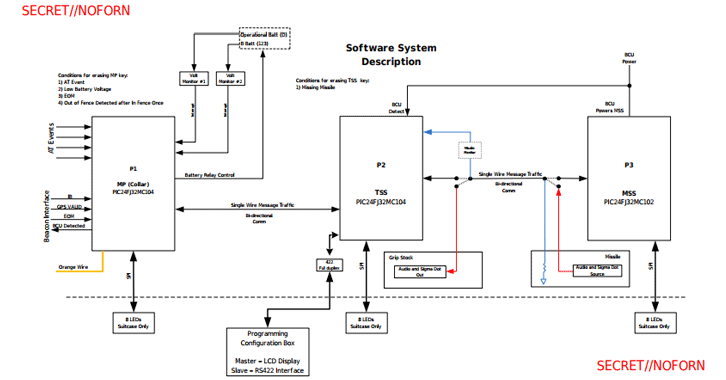
Nicknamed the Project Protego, the PIC-based missile control system is installed aboard a Pratt and Whitney (PWA) aircraft equipped with a missile launch system, allowing it to achieve air-to-air and ground-to-air targets.
The latest leak contains four secret documents in total from the project Protego, along with “37 related documents (hardware/software manuals owned by Microchip Technology Inc.),” WikiLeaks says.
Also Read: Cyber Criminals Are Now Disturbing Cobian RAT Hacking Tool For Free
Exhausted documents reveal the system design, a guide on how to configure and build Protego images, and also suggest that all microcontroller units exchange data and signals in encrypted and authenticated channels.
“The missile system has the Mitsubishi Smart Switch (MSS), the Tube Smart Switch (TSS) and the collar (which holds the missile before and at the time of launch).”
Missiles are activated only when the Master Processor (MP) receives three valid signals from a headlamp, including “In Border”, “Valid GPS” and “End of the operating period”.
WikiLeaks is not sure why the secret documents of the project Protego are part of the repository belonging to the CIA engineering development team, which are apparently known to develop malware and hacking tools for the agency.
In particular, however, the CIA developed the Protego missile control system in collaboration with one of America’s top defense contractors, Raytheon, who was also cited in a previous CIA loss.
Raytheon is the same company the agency has taken for the advanced analysis of malware and the hacking techniques used in the game by hackers and cybercriminals.
It seems that the name, Protego, has been inspired by the magic charm of the shield used in the Harry Potter films, which has aided physical as well as magical attacks.
If so, the main objective of this missile control system could be to defend something (secret or base) from external physical attacks.
Previous Leak Vault 7
Last week, WikiLeaks released another CIA project Protego, dubbed Angelfire, which is a facility developed by the agency to deploy a persistent backdoor on Windows target computers by modifying its partition boot sector.
Since March, WikiLeaks has released 23 series of “Vault 7” series, which includes the most recent leaks and recent weeks, along with the following lots:
ExpressLane – detailed about the spy software the agency used to spy on its intelligence partners around the world, including the FBI, DHS, and NSA.
CouchPotato – A CIA project Protego that has revealed its ability to spy video streams in real-time remotely.
Also Read: Over 28 Million User Data Exposed In Massive Taringa Data Breach
Dumbo – A CIA project that revealed the CIA’s ability to eliminate and manipulate microphones and cameras to corrupt or erase recordings.
Imperial – A CIA project that has announced the details of at least three hacking tools and facilities designed by the CIA to design computers running Apple Mac OS X and various types of Linux.
UCL / Raytheon – A CIA entrepreneur who has analyzed malware and hacking in the wild to help the agency develop its own malware.
Highrise – A supposed CIA project that allows the spy agency to collect and send stolen smartphone data committed to its server via SMS.
BothanSpy and Gyrfalcon – Two installations that allowed CIA agents to intercept and extract SSH credentials from target Windows and Linux systems using different attack vectors.
Outlaw Country– An alleged CIA project that has allowed the spy agency to hack and spy on remote PCs running Linux OS.
Also Read: 6 Million Celebrities Accounts Data Are Up For Sale On Doxagram By Instagram Hacker
ELSA – CIA has declared a malicious program that allows the agency to monitor the geolocation of laptops and PCs running the Microsoft Windows operating system.
Brutal Kangaroo – An assortment of tools for the Microsoft Windows operating system used by CIA agents to identify air-gap equipment within an organization or business without the need for direct access.
Cherry Blossom – A framework used by the CIA to monitor specific Internet activities by exploiting vulnerabilities in Wi-Fi devices.
Pandemic – A CIA project that has allowed the US intelligence agency to transform Windows file servers into secret attack machines that can silently infect other systems within the same network.
Athena – A framework that the agency has designed to remotely spy and take full control of Windows infected systems and works on every version of the Windows operating system from Windows XP to Windows 10.
After Midnight and Assassin – Two alleged CIA malware systems for Microsoft Windows designed to monitor and report actions on the infected remote host PC and perform malicious tasks.
Also Read: A New Gazer Backdoor Is Targeting Ministries and Embassies Around The World
Archimedes – man-to-center attack tool that was developed by the spy agency to locate PCs within a local area network (LAN).
Scribbles – Software supposedly designed to incorporate “beacon web” into confidential documents, causing CIA agents to track initiates and whistleblowers.
Grasshopper – A framework that allows the spy agency to easily create custom malware to break the Windows operating system and avoid antivirus protection.
Marble – source code for a secret anti-forensic tool used by the spy agency to hide the actual source of your malware.
Dark Matter – Some hacking exploits the espionage agency for iPhone and Mac.
Weeping Angel – A spy tool used by the intelligence agency to infiltrate smart TVs and transform them into secret microphones.
Year Zero – CIA piracy takes advantage of popular hardware and software.



