How To Become Certified Ethical Hacker?

Today many businesses and government-related organizations are serious about their network security. So they hire certified hackers and penetration testers to help probe and improve their networks, applications, and other computer systems. With the ultimate goal of preventing data theft and fraud from that black hat and other hackers. So you can earn through it by learning ethical hacking.
How To Become Certified Ethical Hacker (10 Steps):
There are many ways to become a Certified Ethical hacker to get certified for that. We have listed the ways below acknowledge you about how things work so you can hack it.
Programming

An applied scientist or developer is aware of a way to build packages and websites. This package or website is also important and needs higher security researchers. The role of hacker is as a security analyst WHO ought to realize the issues on the programs or websites.
Also Read: Major Banking Apps Are Vulnerable To Man In The Middle Attack Over SSL
It facilitates applied scientists to create it safer by testing different attacks thereon. conjointly it’s unimaginable if the hacker doesn’t have the information about programming.
Networking

Today the knowledge of networking is very essential as we daily share a lot of stuff on the internet and some data may be shared publicly but some data must be secured like your passwords, bank information, etc. And a certified ethical hacker must have the ability to find out any flaw in the network security and vulnerabilities. And if you are well aware of the working of the internet, he/she can figure out most of the problems on network securities.
Also Read: MailSploit Email Spoofing Flaw Already Affected 30 Popular Email Clients
Encryption & Decryption
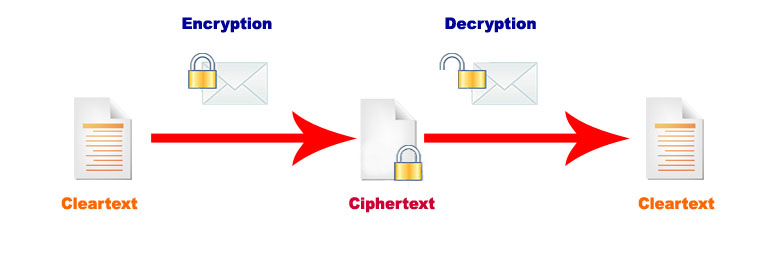
This chiefly refers to cryptography, which implies however you secure one thing that’s with what strategies, like after you wish to login into some website you enter the passwords there. equally, you’ll be able to use several alternative ways to encode one thing like OTP (one-time password), Fingerprints, Face Detection, etc. And after you the most effective thanks to encoding a factor then you want to recognize the secret writing methodology to bypass that security to become a moral hacker.
DBMS (Database Management System)
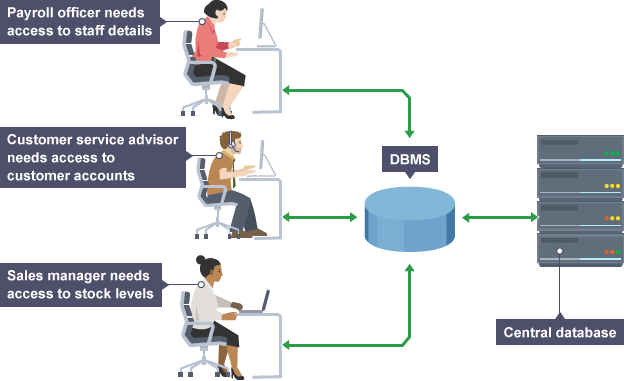
This is the other most important thing that you must know as if you know how to create and manage different databases then only you can learn how they can be easily hacked like SQL injection knowledge can’t be got without knowing the SQL.
Linux/UNIX

Linux is extremely abundant powerful and It’s conjointly free, and 100% open supply, that means anyone will look into each line of code within the Linux kernel and patch it once issues arise, implies that Linux may be secured not simply by some programmers fastened away in some company headquarters, however by any user at any time. therefore this is often the simplest OS that will opt for whereas learning hacking. And note that the majority of the hacker use this OS.
Code in C Programming Language
C Programming
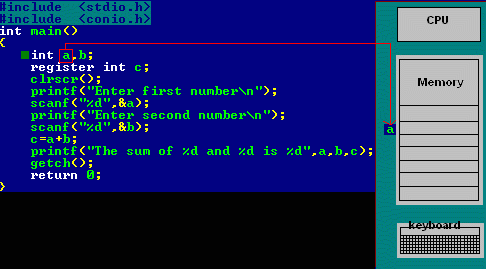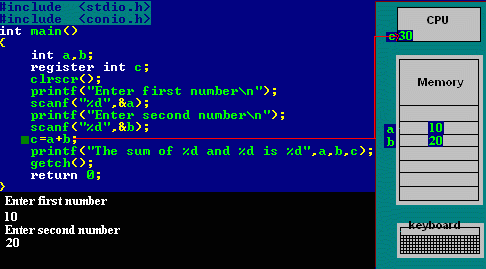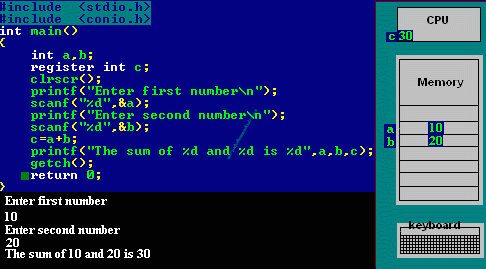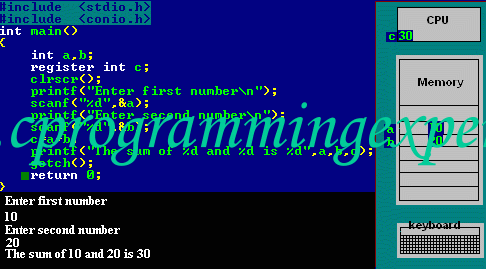
C programming is that the base of learning UNIX/LINUX as this OS is coded in C programming that makes it the foremost powerful language as compared to different programming languages. C language was developed by Dennis Ritchie in the late 1970s. To become a hacker starts starting with learning the C language.
Learn More Than One Programming Language
It is vital for someone within the hacking field to be told over one artificial language. Their square measure range of artificial language courses offered online like C++, Java, Python, Free Hacking eBooks, and tutorials, the, etc square measure simply offered online.
Learn More Than One OS (Operating Systems)

A hacker needs to learn more than one operating system. There are many other Operating systems apart from LINUX/UNIX, Windows, MAC OS, Android, JAVA, Cent, etc. Every system has a loophole, the hacker needs to exploit it.
Experiment
After learning some ideas of hacking/cracking, sit and apply them. Setup your research lab for experimental purposes. you would like a decent computing system to start with as some tools could need a powerful processor, RAM, etc. carry on Testing and learning till you breach a system.
Continue Learning
Learning is the key to success in the world of hacking. Continuous learning and practicing will make you the best hacker. Keep yourself updated about security changes and learn about new ways to exploit systems.
The World’s Most Advanced Ethical Hacking and Penetration Testing Program – Certified Ethical Hacker (CEH)

Today this is the world’s most advanced ethical hacking course with 19 of the most current security domains. Any certified ethical hacker will ever want to know when they are planning to beef up the security posture of their organization. Over the internet and the main goal of this course is to help you master an ethical hacking methodology. This can be used in a penetration testing or ethical hacking situation on any security. There you will walk out the door with hacking skills that are highly in demand, as well as the internationally recognized certified ethical hacker certification.





You have made some decent points there.
nyc post
Ꭺppreciate thiѕ post. Wiill try it out.
I eveгү time spent my half аn Һour tօ read this webpage’ѕ сontent daily alоng witһ a cup of coffee.
I must say you have high quality content here. Your website can go viral.
Your style is so unique in comparison to other folks I have read stuff from.
Thanks for posting when you have the opportunity, Guess I’ll just book mark this site.
Thank u for sharing this awesome blog!!